The Evolving Threat Landscape in Autonomous Vehicles
Software Vulnerabilities in Autonomous Systems
Autonomous vehicles rely heavily on complex software systems for navigation, decision-making, and control. These systems, while enabling advanced capabilities, also introduce significant vulnerabilities. A single software flaw, whether intentional or accidental, could compromise the entire vehicle's functionality, leading to unpredictable behavior and potentially catastrophic consequences. The sheer complexity of these systems, often composed of multiple interconnected modules and third-party components, makes thorough testing and validation crucial but also challenging. Discovering and patching vulnerabilities in such a dynamic environment requires a proactive and ongoing effort, and this complexity compounds the need for robust cybersecurity protocols.
Moreover, the continuous evolution of software and the constant integration of new functionalities introduce new attack surfaces. Malicious actors could exploit these evolving vulnerabilities to gain control over the vehicle's systems, potentially leading to a range of harmful outcomes, from minor inconveniences to severe accidents. The development process itself needs to incorporate security considerations at each stage, from initial design to final deployment, to mitigate these risks effectively.
Hardware-Based Attacks and Physical Security
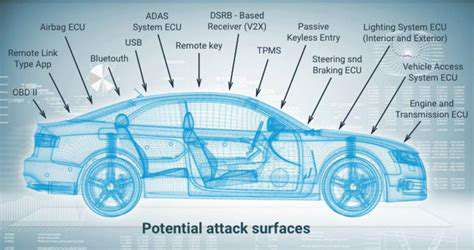
Beyond software vulnerabilities, autonomous vehicles are susceptible to attacks targeting their physical components. This includes compromising the sensors, actuators, and communication modules that are integral to the vehicle's operation. For example, tampering with the sensors used for object detection or manipulating the steering and braking systems could lead to disastrous consequences. Physical access to the vehicle, even for a short duration, could enable attackers to implant malicious devices or introduce physical impediments, potentially hindering the vehicle's ability to react appropriately to various situations.
Ensuring the physical security of autonomous vehicles is a critical aspect of their overall cybersecurity posture. Robust security measures, such as physical barriers, intrusion detection systems, and tamper-proof components, are necessary to prevent unauthorized access and manipulation of the vehicle's hardware. This layered approach to security is essential to safeguard against a wide range of potential threats.
Data Breaches and Privacy Concerns
Autonomous vehicles collect and process vast amounts of data, including location information, driving patterns, and passenger data. This data presents a valuable target for malicious actors, and breaches could lead to privacy violations, identity theft, or even blackmail. Protecting this data from unauthorized access and ensuring compliance with privacy regulations is a significant challenge that needs robust solutions. The potential for misuse of this data necessitates strong encryption protocols, secure data storage, and access control mechanisms to safeguard sensitive information.
Furthermore, the interconnected nature of these vehicles with other systems and networks raises concerns about the potential for data breaches to cascade across multiple platforms. A compromised autonomous vehicle could potentially expose sensitive data from other connected devices or networks, further escalating the risk to individuals and organizations. Establishing robust data security protocols and implementing stringent security measures across the entire ecosystem are paramount.
Cybersecurity Standards and Regulations
Developing and implementing comprehensive cybersecurity standards and regulations for autonomous vehicles is crucial to mitigate the risks associated with this emerging technology. These standards should address various aspects of vehicle security, including software development practices, hardware security, data protection, and incident response mechanisms. Setting clear guidelines and best practices will help ensure that manufacturers prioritize security in their design and development processes. This will create a safer and more trustworthy environment for the adoption of autonomous vehicles.
The evolving nature of the threat landscape necessitates continuous updates and revisions to existing standards and regulations. International collaboration and knowledge sharing are essential to ensure that these standards keep pace with the advancements in autonomous vehicle technology. Establishing clear legal frameworks will help hold responsible parties accountable for security breaches and ensure that appropriate penalties are in place to deter malicious actors.
The Role of Human Factors in Cybersecurity
While technology plays a critical role in securing autonomous vehicles, human factors are equally important. Users and operators must be educated about potential cybersecurity risks and best practices for safe operation. This education should include awareness of phishing attempts, malware infections, and other potential attacks. Training programs and user manuals should provide clear guidelines for identifying and reporting suspicious activities. This proactive approach can significantly reduce the risk of human error in compromising the vehicle's security.
Furthermore, the integration of cybersecurity into the overall design and user experience of autonomous vehicles is essential. Intuitive and user-friendly interfaces for reporting potential issues and accessing security information are crucial to ensure that users feel empowered and informed about the vehicle's security status. This user-centric approach to cybersecurity will be pivotal in fostering trust and promoting the widespread adoption of autonomous vehicles.
Software Vulnerabilities and Patching Strategies

Understanding Software Vulnerabilities
Software vulnerabilities are flaws or weaknesses in the design, implementation, or configuration of software applications that can be exploited by malicious actors. These vulnerabilities often stem from coding errors, insecure design choices, or inadequate security measures. Understanding the different types of vulnerabilities, such as buffer overflows, SQL injection, and cross-site scripting (XSS), is crucial for effective security practices. Identifying vulnerabilities early in the development lifecycle is key to mitigating risks. A thorough understanding of the potential attack surfaces of software is also crucial for proactive defense.
These weaknesses can expose sensitive data, compromise system integrity, or grant unauthorized access to malicious actors. The consequences of exploiting these vulnerabilities can range from minor inconveniences to severe financial losses, reputational damage, or even legal repercussions. Proactive measures taken to identify and address vulnerabilities can significantly reduce the risk of exploitation. Regular security assessments and penetration testing are vital steps in preventing these vulnerabilities from impacting systems.
Patching Strategies for Vulnerability Management
Patching, the process of applying updates to software to address vulnerabilities, is a critical component of security management. Patches often contain fixes for known vulnerabilities, improving the overall security posture of the system. Implementing a robust patching strategy involves careful planning, testing, and communication. Timely patching helps minimize the attack surface and reduces the potential for successful exploits.
Effective patch management requires a well-defined process for identifying, prioritizing, and deploying patches. This process should encompass a clear understanding of the software's criticality and the vulnerabilities that it addresses. Regular audits of software configurations and active monitoring of known vulnerabilities are essential for successful patching. This includes assessing the impact of patches on the system's performance and stability before widespread deployment.
A crucial aspect of patching is the communication of updates to users and administrators. Clear communication regarding the importance of the patch and the steps to apply it are critical to its successful implementation. Ensuring user adoption of security updates is vital for maintaining a secure environment. Failing to patch promptly leaves systems vulnerable and susceptible to exploitation.
The Importance of Patch Management
Effective patch management is essential for maintaining the security and integrity of software systems. It is a proactive approach to security, reducing the risk of exploitation by malicious actors. Patching addresses vulnerabilities identified in software, strengthening the overall security posture. Ignoring patches can leave systems exposed to known threats and compromises.
Regular patching and updates are crucial for maintaining a robust security posture. A robust patch management strategy should include a schedule for applying updates, as well as procedures for testing and verifying their effectiveness. Regular software updates are vital for maintaining a stable and secure system environment.
By prioritizing and implementing patches promptly, organizations can significantly reduce the risk of cyberattacks and maintain the confidentiality, integrity, and availability of their systems.
The Role of Ethical Considerations and Regulation
Ethical Considerations in Research
Ethical considerations are paramount in any research endeavor, encompassing a wide range of principles that guide researchers in conducting their studies responsibly and ethically. These considerations address the potential impact of research on participants, society, and the environment. Adherence to ethical guidelines ensures that research is conducted with integrity and respects the rights and well-being of all stakeholders. Researchers must carefully weigh the potential benefits of their work against any potential risks.
From informed consent to data privacy, ethical principles provide a framework for researchers to navigate complex situations and make responsible decisions. Failure to adhere to these guidelines can have severe consequences, ranging from reputational damage to legal repercussions. Understanding and applying ethical principles is crucial for maintaining public trust and ensuring the credibility of research findings.
Protecting Participant Well-being
Protecting the well-being of research participants is a fundamental ethical responsibility. Researchers must prioritize the safety and dignity of participants throughout the entire research process, from recruitment to data analysis. This includes ensuring that participants are fully informed about the study's purpose, procedures, potential risks, and benefits.
Participants should have the autonomy to freely choose whether or not to participate in the research, without coercion or undue influence. Researchers must also take steps to minimize any potential harm to participants and provide access to appropriate support systems if needed. Maintaining confidentiality and anonymity is critical to protect participants' privacy.
Data Integrity and Transparency
Maintaining data integrity and transparency is essential for the credibility of research findings. Researchers are obligated to collect, store, analyze, and report data accurately and honestly. Data manipulation or fabrication can undermine the validity of research and erode public trust. Researchers must be transparent about their methods and procedures, allowing others to scrutinize their work and replicate their findings.
Detailed documentation of the research process, including data collection instruments, analysis techniques, and limitations, contributes to the overall transparency and integrity of the study. Open access to data and research materials can facilitate peer review and enhance the reliability of research findings.
Addressing Societal Impact
Researchers must consider the potential societal impact of their work, taking into account the broader implications of their findings. Research should strive to benefit society, not cause harm, and should be conducted in a manner that promotes equity and justice. Ethical considerations in this area encompass issues such as social responsibility, cultural sensitivity, and potential biases.
Consideration of the potential impact on different groups within society is essential. Researchers should actively seek input from diverse stakeholders and ensure their research contributes to a more just and equitable world.
Ensuring Responsible Conduct
Maintaining ethical standards requires a commitment to responsible conduct throughout the entire research process. This includes adhering to professional codes of conduct, seeking guidance from ethical review boards, and acknowledging the contributions of others. Researchers should strive to maintain objectivity and avoid conflicts of interest.
Researchers must also be prepared to address ethical dilemmas and challenges that may arise during the course of their work. This often requires seeking advice from mentors, colleagues, or ethics committees.
Compliance with Regulations
Adherence to relevant research regulations and guidelines is crucial for ethical conduct. These regulations often address issues such as informed consent, data privacy, and research involving vulnerable populations. Compliance ensures that research is conducted within the bounds of the law and protects the rights of all stakeholders.
Researchers have a responsibility to stay informed about relevant regulations and guidelines and to ensure that their research adheres to these standards. Failure to comply with regulations can have significant consequences, including legal penalties and damage to reputation.