The Human Factor in Security Breaches
Automotive cybersecurity isn't just about code - it's about people. Many breaches start with simple human mistakes: a technician using default passwords, an engineer falling for phishing scams, or a driver connecting to unsecured Wi-Fi networks. The human element remains the weakest link in the security chain.
Comprehensive training programs must address both technical staff and end-users. Mechanics need cybersecurity awareness as much as software engineers. Consumers should understand basic precautions like keeping infotainment systems updated and avoiding suspicious third-party apps.
The Impact of Cloud Connectivity
Modern vehicles constantly communicate with manufacturer clouds for updates, diagnostics, and features. This connectivity creates a sprawling attack surface where a single cloud breach could potentially affect thousands of vehicles simultaneously. The recent trend toward over-the-air updates introduces both convenience and risk.
Automakers must implement military-grade encryption for all vehicle-cloud communications. Multi-factor authentication should protect backend systems, while rigorous API security prevents unauthorized access. The cloud infrastructure requires continuous monitoring for unusual activity patterns.
Regulatory Pressures and Standards
Governments worldwide are scrambling to establish automotive cybersecurity regulations. The UN's WP.29 regulations and upcoming ISO/SAE 21434 standard set new benchmarks for vehicle security. Non-compliance isn't just risky - it may soon become illegal to sell vehicles without proper cybersecurity certifications.
Meeting these standards requires fundamental changes in automotive development cycles. Security must be baked in from initial design rather than bolted on as an afterthought. This paradigm shift demands close collaboration between engineers, security experts, and regulators.
AI's Double-Edged Sword
While AI helps detect anomalies in vehicle networks, hackers also weaponize it to find vulnerabilities. Machine learning algorithms can probe systems for weaknesses faster than any human team. The AI security arms race has reached the automotive sector with alarming speed.
Defensive AI must evolve alongside offensive capabilities. Neural networks that predict attack patterns, coupled with blockchain-based firmware verification, may represent the next frontier in vehicle protection. However, over-reliance on AI creates its own vulnerabilities that require careful management.
Vulnerabilities and Attack Vectors in Modern Cars
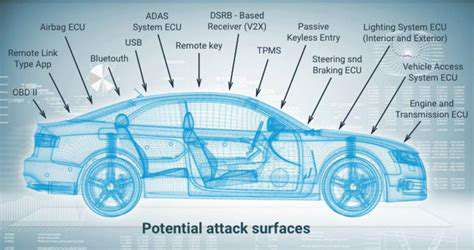
Exploiting Software Weaknesses
Modern vehicles contain millions of lines of code, each potentially hiding critical vulnerabilities. The average luxury car now runs more software than early space shuttles, yet often lacks equivalent security rigor. Zero-day exploits in infotainment systems have become gateway drugs for full vehicle compromise.
Attackers increasingly target the software supply chain, compromising vendor components before they reach assembly lines. The industry's just-in-time manufacturing model leaves little room for thorough security validation. A single vulnerable third-party library could affect entire vehicle fleets.
Network Attack Surfaces
Today's vehicles are rolling networks with multiple entry points: Bluetooth, cellular, Wi-Fi, and even tire pressure monitoring systems. Researchers have demonstrated attacks that start with low-speed CAN buses and escalate to critical driving systems. The interconnected nature amplifies risks - compromising one ECU can provide lateral movement to others.
Diagnostic ports, once only accessible in service centers, now represent glaring vulnerabilities. Wireless diagnostic tools and third-party dongles create new attack vectors that bypass traditional physical security measures. Network segmentation remains inconsistent across manufacturers.
Social Engineering Threats
Hackers increasingly target dealerships and service centers rather than vehicles directly. A single compromised technician's computer can provide access to entire fleets through manufacturer maintenance portals. The growing secondary market for automotive diagnostic tools has put powerful hacking capabilities in amateur hands.
Owners themselves become targets through fake recall notices or malicious vehicle health report phishing schemes. As cars become app platforms, malicious third-party apps could gain dangerous levels of vehicle control while appearing legitimate.
Physical Access Dangers
Keyless entry systems have spawned wave after wave of relay attacks. The arms race between manufacturers and thieves continues to escalate, with some attacks now using software-defined radios to mimic key fobs at unprecedented distances. Some luxury vehicles have become so thief-friendly they're effectively uninsurable in certain markets.
Onboard diagnostics ports, while essential for maintenance, provide direct access to vehicle networks. Physical security measures often fail to prevent access - many ports are readily accessible and lack basic tamper detection. The rise of car hacking toolkits has democratized these attacks.