Data Security and Privacy Concerns: A Crucial Consideration
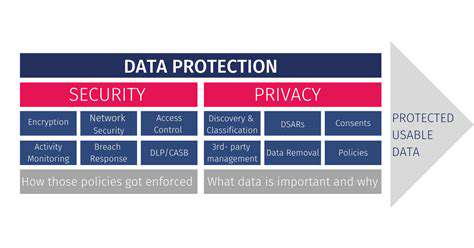
Data Breaches and Their Impact
Data breaches are a significant threat to individuals and organizations alike, resulting in substantial financial losses, reputational damage, and a loss of customer trust. These breaches can expose sensitive personal information, including social security numbers, credit card details, and medical records, leading to identity theft and financial exploitation. The consequences of a data breach can ripple through various sectors, impacting businesses, governments, and even the economy as a whole.
The impact of a data breach extends beyond the immediate financial losses. Reputational damage can take years to repair, significantly impacting the trust customers have in a brand. Furthermore, the legal and regulatory repercussions can be substantial, with organizations facing potential fines and legal actions.
Protecting Sensitive Data
Implementing robust security measures is crucial in mitigating the risk of data breaches. This involves employing strong encryption protocols to protect sensitive data during transmission and storage. Regular security audits and vulnerability assessments are also essential to identify and address potential weaknesses in systems and processes.
Organizations must invest in comprehensive security training for employees to raise awareness about potential threats and best practices for data handling. Strong passwords, multi-factor authentication, and secure network configurations are critical components of a comprehensive security strategy.
Privacy Regulations and Compliance
Data privacy regulations like GDPR, CCPA, and HIPAA have significantly shaped the approach to data security. These regulations mandate that organizations collect, use, and store personal data responsibly and transparently. Adherence to these regulations is essential to avoid significant penalties and maintain the trust of customers and stakeholders.
Understanding and complying with the specific requirements of these regulations is vital for organizations operating in different jurisdictions. This often involves significant investment in infrastructure and processes to ensure ongoing compliance.
The Role of Cybersecurity Professionals
Cybersecurity professionals play a critical role in safeguarding data and preventing breaches. Their expertise in identifying vulnerabilities, implementing security measures, and responding to threats is essential for maintaining a secure digital environment. Effective incident response plans are vital to minimize the damage caused by security incidents and ensure a swift recovery process.
Continuous learning and adaptation to emerging threats are critical for cybersecurity professionals. The ever-evolving nature of cyberattacks demands continuous upskilling and the adoption of new security technologies.
Data Minimization and Usage Restrictions
Data minimization is a crucial principle in data security and privacy. Organizations should only collect and store the minimum amount of data necessary for their legitimate business purposes. This approach helps to reduce the potential attack surface and limits the impact of a potential breach.
The Importance of Data Encryption
Data encryption is a fundamental security measure that protects sensitive information from unauthorized access. By converting data into an unreadable format, encryption renders it unusable for malicious actors. Robust encryption protocols are critical to protect sensitive data during transit and storage. This is especially important for data stored on cloud platforms or transmitted across networks.
Employee Awareness and Training
Employee training and awareness programs are essential components of a comprehensive data security strategy. Educating employees about the importance of data security, common threats, and best practices for data handling can significantly reduce the risk of accidental breaches. Regular training sessions and awareness campaigns can reinforce good security habits and reduce the likelihood of human error leading to security incidents.
The Future of Data Monetization in the Connected Car Industry
Data-Driven Insights and Value Creation
The connected car, with its wealth of data generated from sensors, navigation, and driver behavior, presents a significant opportunity for monetization. This data, when analyzed and interpreted correctly, provides invaluable insights into driving patterns, vehicle performance, and even driver preferences. These insights can be leveraged to create personalized services, improve safety features, and enhance the overall vehicle ownership experience for consumers. By understanding how drivers interact with their vehicles, manufacturers can develop targeted marketing strategies and tailor services to meet specific needs, creating a virtuous cycle of data-driven improvement.
Furthermore, the data generated by connected car systems can be used to develop new revenue streams. For example, predictive maintenance, based on real-time sensor data, can significantly reduce repair costs for both manufacturers and consumers. This proactive approach to maintenance not only saves money but also enhances the reliability and longevity of the vehicle. The data can also be used to develop new insurance models that offer personalized premiums based on individual driving habits.
Developing Innovative Monetization Models
Moving beyond traditional methods of revenue generation, the connected car industry needs to embrace innovative monetization models. Subscription-based services, offering features like enhanced safety, personalized navigation, or premium entertainment, are becoming increasingly popular. Partnerships with third-party applications and services can also expand the range of monetization options.
Developing a robust data monetization strategy requires careful consideration of consumer privacy and data security. Clear and transparent policies regarding data collection, usage, and sharing are essential to build trust and maintain customer loyalty. Implementing strong encryption protocols and adhering to relevant data protection regulations are crucial to safeguarding sensitive information.
The Role of Data Security and Privacy
Data security and privacy are paramount in the connected car industry. As vehicles become increasingly reliant on interconnected systems, the potential for data breaches and unauthorized access significantly rises. Robust cybersecurity measures are essential to protect sensitive information from malicious actors. This includes implementing strong encryption, regular security audits, and proactive threat detection systems.
Transparency and control over data usage are critical. Drivers should have clear insight into how their data is being collected, used, and shared. Providing users with the ability to opt out of certain data collection or customize data sharing preferences builds trust and fosters a positive relationship between the manufacturer and the customer.
The Impact on Automotive Manufacturers and Consumers
The future of data monetization in the connected car industry will significantly impact both automotive manufacturers and consumers. Manufacturers will need to invest in data analytics capabilities and develop innovative services to leverage the data generated by connected vehicles. This includes developing sophisticated algorithms to interpret sensor data, creating user-friendly interfaces to access personalized services, and establishing secure platforms to protect data integrity.
Consumers will benefit from enhanced vehicle features, personalized services, and potentially reduced costs through predictive maintenance and optimized insurance models. However, it is crucial for manufacturers to maintain transparency and provide clear guidelines regarding data usage to maintain consumer trust and confidence in connected car technology.