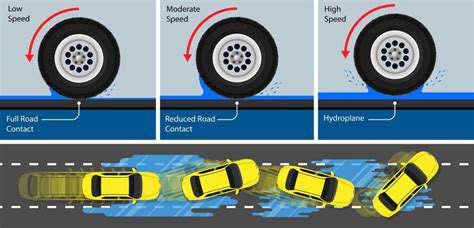
Self-driving cars, commonly referred to as autonomous vehicles, are advancing at a remarkable pace, offering the prospect of safer and more streamlined transportation systems. These innovative machines rely on an intricate network of sensors, cutting-edge algorithms, and powerful computational resources to interpret road conditions, circumvent obstacles, and execute driving maneuvers. While this emerging technology holds tremendous promise, it simultaneously introduces a host of ethical quandaries that demand thorough analysis and public discourse.
The Potential for Enhanced Safety
A primary advantage of autonomous vehicles lies in their capacity to minimize traffic incidents. By eliminating the human factor from driving operations, these vehicles could dramatically decrease the occurrence of road fatalities and severe injuries. This safety advantage highlights the critical need to thoughtfully address the ethical challenges accompanying their implementation and widespread use.
The Ethical Dilemma of Accidents
Despite their safety objectives, autonomous vehicles present complex liability questions when accidents occur. Determining accountability - whether it rests with manufacturers, software engineers, or vehicle owners - constitutes a significant ethical challenge. Establishing unambiguous liability frameworks remains imperative to maintain justice and responsibility in this fast-changing technological environment.
Data Privacy and Security Concerns
Self-driving cars generate extensive data regarding their operational environment and driving behaviors. This mass data collection raises serious privacy issues, especially concerning potential exploitation by external entities. Implementing stringent data protection protocols and transparent information management practices becomes crucial to safeguard personal privacy rights in the era of autonomous transportation.
The Impact on Employment and the Economy
The broad integration of self-driving vehicles could dramatically transform job markets, particularly affecting professional drivers in transportation sectors. This technological shift necessitates forward-looking economic strategies, including comprehensive retraining initiatives and social support systems for displaced workers. The extended economic consequences of this transition require careful evaluation and planning.
Accessibility and Equity Considerations
Guaranteeing fair access to autonomous vehicle technology for all societal segments remains paramount. Addressing cost barriers, infrastructure availability, and potential technological disparities is essential to prevent the exacerbation of existing social inequalities. Ethical concerns regarding equitable access must remain central to technological development processes.
The Role of Regulation and Policy
Developing comprehensive regulatory frameworks proves critical for guiding the responsible advancement of autonomous vehicles. These frameworks must encompass safety protocols, liability structures, data protection measures, and ethical guidelines. Coordinated efforts among government bodies, technology firms, and the general public are necessary to ensure the ethical development and deployment of these vehicles.

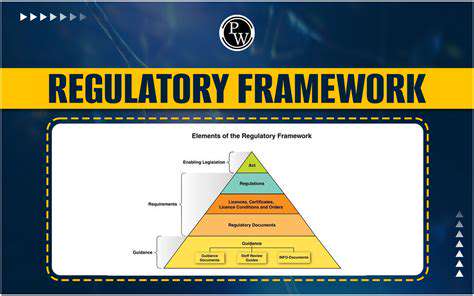
The Role of Ethical Hacking and Security Protocols
Ethical Hacking: A Necessary Component in Cybersecurity
Penetration testing, alternatively termed ethical hacking, represents an indispensable practice within the dynamic field of cybersecurity. This process involves authorized attempts to identify and exploit system vulnerabilities before malicious actors can capitalize on them. This preventive methodology enables organizations to reinforce their digital defenses and safeguard confidential information against advanced cyber threats. Through simulated attacks, security professionals can detect system weaknesses and implement corrective measures prior to actual breaches occurring, proving far more economical than post-breach remediation.
Identifying and Patching Vulnerabilities
A fundamental aspect of ethical hacking involves the detection of system vulnerabilities. Security specialists employ diverse tools and methodologies to uncover potential weaknesses, including outdated software, improper configurations, and programming flaws. Early identification of these vulnerabilities permits timely remediation, substantially decreasing the likelihood of successful cyberattacks. Comprehensive security evaluations enable organizations to implement appropriate safeguards and cultivate a proactive security posture.
Improving Security Policies and Procedures
Ethical hacking contributes significantly to the enhancement of organizational security frameworks. By revealing system weaknesses, security professionals provide valuable guidance for strengthening protective measures. Developing comprehensive security protocols remains essential for countering the constantly evolving landscape of cyber threats.
Testing Security Measures
Ethical hacking serves as a critical evaluation tool for existing security infrastructure. Through simulated cyberattacks, organizations can assess the effectiveness of their security controls, including firewalls and intrusion detection systems, ensuring these measures adequately prevent unauthorized access and data compromise.
Enhancing Security Awareness
The knowledge derived from ethical hacking exercises can significantly improve organizational security consciousness. Educating employees about potential attack methods, including phishing schemes and social engineering tactics, proves vital for establishing a robust security culture. When staff members understand common cyber threats, they become better equipped to identify and report suspicious activities.
Staying Ahead of Evolving Threats
As cybersecurity threats continue to evolve and diversify, ethical hacking enables organizations to maintain a defensive advantage. Continuous system evaluation and testing allow for the adaptation of security strategies to address emerging vulnerabilities. Proactive security measures are indispensable for ensuring business continuity and protecting sensitive organizational data against increasingly sophisticated cyberattacks.