Data Security and Privacy Concerns
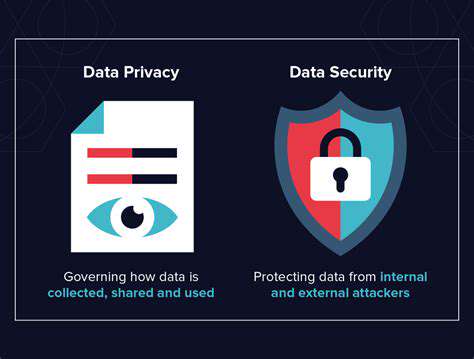
Data breaches and their impact
Modern digital systems face growing vulnerabilities as cybercriminals develop increasingly sophisticated attack methods. The exposure of personal data through security lapses can trigger cascading consequences, from financial fraud to psychological trauma. Beyond individual victims, organizational credibility often suffers lasting damage when customer trust erodes following high-profile incidents. Implementing comprehensive protective measures while understanding system weaknesses forms the foundation of effective risk management.
Compromised databases may contain everything from banking details to private medical histories, with consequences ranging from minor annoyances to life-altering disruptions. The severity depends on multiple factors including the sensitivity of exposed information and the number of affected parties.
Protecting sensitive data
Safeguarding confidential information demands a strategic combination of technical and human solutions. Advanced encryption methods should protect data during transmission and storage. Businesses must establish strict access management systems while continuously monitoring for unusual activity patterns. Comprehensive staff education programs help combat social engineering attempts and internal security threats.
Periodic security evaluations and simulated attacks reveal system vulnerabilities before criminals can exploit them. These preventative measures help maintain robust defenses against evolving digital threats, potentially stopping breaches before they occur.
Privacy regulations and compliance
Global data protection laws like GDPR and CCPA impose rigorous requirements on organizations handling personal information. These frameworks mandate clear disclosure of data practices while giving individuals greater control over their digital footprints. Non-compliance can lead to substantial financial penalties and lasting reputational harm.
Adhering to privacy regulations demonstrates organizational commitment to ethical data practices. Companies must regularly review and update their procedures to align with changing legal requirements, ensuring continued compliance across all operations.
The role of encryption
Modern encryption transforms readable information into coded formats that resist unauthorized interpretation. Implementing advanced encryption standards represents a critical defense against data interception and theft. Effective key management practices enhance the security of encrypted systems, providing additional protection layers for sensitive information.
Security awareness training
Human factors remain among the most significant security vulnerabilities. Regular educational initiatives should teach personnel to identify phishing attempts, suspicious links, and other common attack vectors. Ongoing training updates keep staff informed about emerging threats and evolving best practices.
Building a security-conscious workplace culture reduces risks associated with human error. Consistent reinforcement of security protocols through various communication channels helps maintain vigilance across all organizational levels.
Cybersecurity threats
The digital threat landscape continues evolving with increasingly complex malware and targeted attacks. Proactive defense strategies including timely system updates, advanced monitoring tools, and detailed incident response plans help organizations stay ahead of potential breaches. Continuous threat intelligence gathering allows for adaptive security postures.
Effective cybersecurity combines technological solutions with human expertise. Encouraging employee participation in security processes creates additional detection layers while fostering organizational resilience against digital threats.
Infrastructure and Road Standards
Infrastructure Considerations for Autonomous Vehicles
Successful autonomous truck deployment requires careful evaluation of current transportation infrastructure. Existing roads and signage systems often lack optimization for self-driving technology, necessitating upgrades in multiple areas. Enhanced lane markings, standardized traffic control devices, and potential dedicated autonomous vehicle corridors could improve safety and efficiency. These infrastructure improvements will facilitate smoother integration of autonomous trucks into existing transportation networks.
Standardization of Roadway Designs
Consistent roadway specifications across jurisdictions enable more reliable autonomous vehicle performance. Variations in road geometry, intersection designs, and signage between regions create navigation challenges for automated systems. Developing unified design standards at national or regional levels would enhance operational predictability for autonomous trucking fleets.
Safety Protocols and Regulations
Comprehensive safety frameworks must govern all aspects of autonomous truck operations. These should address vehicle design specifications, testing requirements, and operator qualifications. Clear incident response protocols and liability determination processes will provide necessary legal certainty for all stakeholders involved in autonomous transportation systems.
Addressing Intersection Management
Autonomous vehicles require specialized intersection navigation capabilities that differ from human drivers. Developing standardized intersection designs and signal protocols will enhance safety while improving traffic flow efficiency. These systems must account for complex interaction scenarios between autonomous and conventional vehicles.
Maintenance and Repair Standards for Infrastructure
Well-maintained roadways prove essential for reliable autonomous vehicle operation. Degraded infrastructure can impair sensor accuracy and navigation reliability. Implementing rigorous maintenance schedules and quality standards will support consistent performance of autonomous trucking systems.
Data Collection and Analysis for Road Conditions
Comprehensive environmental data gathering enhances autonomous vehicle capabilities. Detailed information about pavement conditions, weather patterns, and traffic dynamics allows for more informed navigation decisions. Sustainable data collection methods should balance information needs with environmental considerations.
Public Awareness and Education Initiatives
Successful autonomous truck integration requires public understanding and acceptance. Educational programs should clearly explain technology capabilities, safety features, and operational parameters. Transparent communication about benefits and limitations helps build societal confidence in autonomous transportation solutions.
Operational and Safety Standards for Autonomous Trucking
Defining Operational Standards
Comprehensive operational guidelines form the foundation for safe autonomous truck deployment. These standards should address vehicle maintenance requirements, software update protocols, and vehicle-to-infrastructure communication standards. Detailed documentation and extensive testing procedures ensure consistent performance across diverse operating conditions. Well-defined operational parameters promote public confidence in autonomous transportation technology.
Specific performance metrics including speed management, braking characteristics, and emergency procedures require clear definition. Operational standards must account for variable environmental conditions and traffic scenarios to ensure predictable vehicle behavior in all situations.
Safety Protocols and Mitigation Strategies
Redundant safety systems provide critical fail-safes for autonomous truck operations. Backup mechanisms for essential functions enhance reliability during system anomalies. Integrated advanced driver assistance features supplement core autonomous systems, providing additional safety layers. Comprehensive testing across diverse scenarios identifies potential failure modes before commercial deployment.
Systematic incident analysis processes enable continuous safety improvement. Dedicated investigation teams should examine operational anomalies to implement preventive measures. Data-driven risk assessment methodologies support proactive safety enhancements throughout the vehicle lifecycle.
Data Security and Privacy Regulations
Autonomous systems generate extensive operational data requiring robust protection. Multi-layered security measures including encryption and access controls safeguard sensitive information. Clear data governance policies ensure responsible handling of personal information collected during vehicle operations.
Transparent data practices build public trust in autonomous technologies. Regulatory frameworks should balance operational data needs with individual privacy rights, establishing clear guidelines for data collection and usage.
Liability and Insurance Frameworks
Clear liability determination processes are essential for autonomous vehicle incidents. Legal frameworks must define responsibility allocation between manufacturers, operators, and technology providers. Specialized insurance products should address unique risks associated with autonomous truck operations while ensuring adequate victim compensation.
Testing and Validation Procedures
Rigorous testing protocols verify autonomous system reliability across operating conditions. Extensive simulation and real-world evaluation identify performance limitations before commercial deployment. Phased testing approaches allow for incremental validation of system capabilities while managing operational risks.
Public Acceptance and Community Engagement
Transparent technology demonstrations and educational initiatives address public concerns about autonomous trucks. Stakeholder engagement programs facilitate dialogue about potential economic and social impacts. Proactive community involvement helps shape responsible deployment strategies that consider local needs and concerns.
Comprehensive impact assessments evaluate potential workforce effects and infrastructure requirements. Development of transition strategies helps mitigate potential negative consequences while maximizing societal benefits from autonomous transportation technologies.