Protecting Your Connected Car: Mitigation Strategies
Protecting Your Connected Car Data
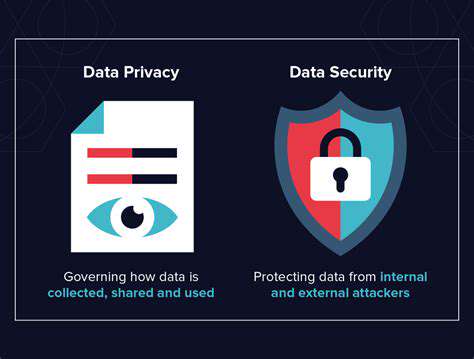
Modern vehicles generate staggering amounts of sensitive data – from precise location tracking to detailed driving behavior analytics. This information, if compromised, could enable everything from financial fraud to physical stalking. Recognizing these risks represents the essential first step in building effective defenses for your connected vehicle.
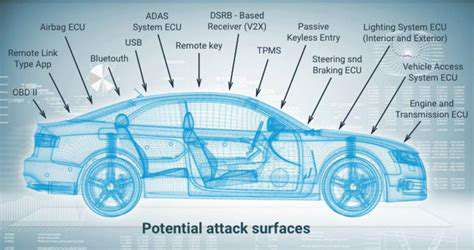
As automotive technology advances, each new feature introduces potential vulnerabilities. The convenience of connected cars comes with inherent security tradeoffs that demand careful consideration and proactive management. Vehicle owners must take active responsibility for understanding and mitigating these risks.
Effective protection involves multiple layers: complex unique passwords, prompt software updates, and ongoing security awareness. Regularly auditing your vehicle's data collection and sharing settings provides critical visibility into potential exposure points.
Security Measures for Connected Cars
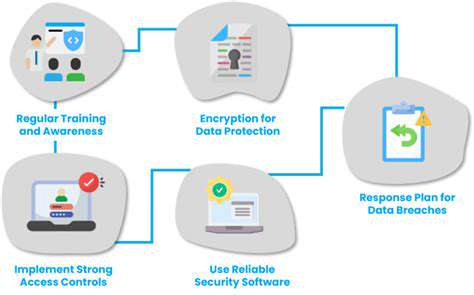
Vehicle cybersecurity requires a comprehensive approach. Begin with strong, distinct passwords for all connected services – never reuse credentials across platforms. Manufacturers frequently release critical security patches, so enabling automatic updates ensures your vehicle's software remains protected against emerging threats.
Scrutinize your car's privacy controls to understand exactly what data gets collected and shared. Many remote access features, while convenient, create potential entry points for attackers if not properly secured. Disable any unnecessary connectivity options to minimize your exposure.
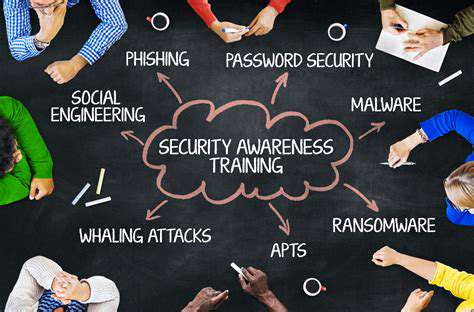
Remain vigilant against social engineering attempts targeting vehicle owners. Legitimate automotive companies will never request sensitive information via unsolicited messages – treat such communications with extreme skepticism.
The Future of Cybersecurity in the Automotive Industry

The Evolving Threat Landscape
The pace of cyber threat evolution continues accelerating, with attackers leveraging cutting-edge technologies like AI to develop increasingly sophisticated attacks. Organizations must adopt equally advanced, adaptive security strategies to counter these developing dangers.
Traditional security measures alone no longer suffice. Effective modern defense requires integrated protection spanning networks, endpoints, and cloud environments, complemented by comprehensive incident response capabilities.
The Role of Artificial Intelligence
AI-powered security tools can process enormous datasets to detect subtle attack patterns human analysts might miss. This machine learning capability enables near-real-time threat identification and response, dramatically improving defensive effectiveness.
However, AI implementation requires careful oversight. Ethical considerations around data usage and algorithmic bias demand serious attention to ensure responsible AI deployment in security applications.
The Importance of Human Factors
Despite technological advances, people remain both the weakest link and strongest asset in cybersecurity. Comprehensive security training programs that cultivate a culture of vigilance can transform employees from vulnerabilities into an organization's first line of defense.
Well-designed security systems account for human fallibility through clear procedures, fail-safes, and regular audits. Balancing user convenience with robust protection remains an ongoing challenge for security professionals.
The Future of Cybersecurity Regulations
Global regulatory frameworks continue evolving to address emerging cyber risks. Maintaining compliance requires ongoing effort as standards frequently update to reflect new threat intelligence and technological developments.
International cooperation grows increasingly vital as cyber threats recognize no borders. Coordinated global standards and information sharing provide the most effective defense against transnational cybercrime networks.