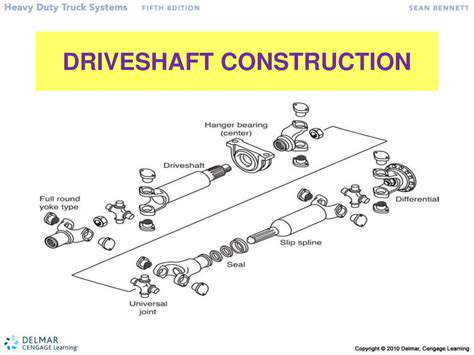
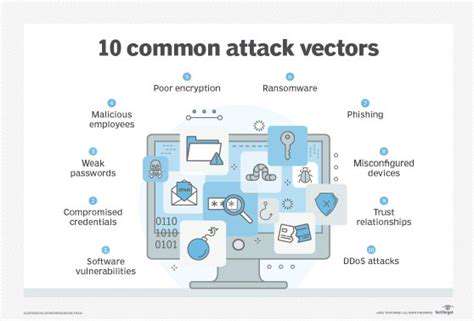
Exploiting Connectivity: Common Attack Vectors
Leveraging Network Effects
Modern digital ecosystems thrive on interconnected relationships. Organizations that successfully harness these dynamics often experience accelerated expansion and competitive advantages. Strategic utilization of network effects can transform operational capabilities and market positioning. Robust platforms create self-reinforcing cycles where increased participation drives greater value for all users.
This interdependence enables unprecedented resource sharing and collective problem-solving. Access to diverse expertise and perspectives significantly shortens development cycles for innovative solutions.
Enhanced Communication and Collaboration
Digital connectivity has redefined workplace interactions by eliminating geographical constraints. Teams now maintain continuous coordination through advanced communication tools, enabling instantaneous information exchange across time zones. These technological advancements have fundamentally altered business operations, permitting more agile responses to market demands.
The shift toward distributed workforces requires reliable digital infrastructure. Companies benefit from accessing specialized skills globally while maintaining operational cohesion through virtual collaboration platforms.
Improved Customer Engagement
Contemporary businesses maintain direct, continuous dialogues with their clientele through multiple digital channels. These interactions provide valuable opportunities to understand customer needs, address concerns promptly, and cultivate lasting brand relationships.
Organizations that prioritize customer feedback demonstrate higher retention rates and stronger brand advocacy. This customer-centric approach directly contributes to sustainable revenue growth and market differentiation.
Data-Driven Insights
Modern enterprises leverage vast data streams to inform strategic decisions. Sophisticated analytical tools reveal behavioral patterns and emerging trends that guide product development and operational improvements.
Advanced analytics empower organizations to anticipate market shifts and optimize resource allocation with unprecedented precision. This analytical capability represents a critical competitive advantage in rapidly evolving industries.
Expanding Market Reach
Digital connectivity dissolves traditional market boundaries, enabling businesses to engage customers worldwide. This global access creates opportunities for revenue diversification and cultural adaptation of products and services.
International expansion requires careful consideration of local preferences and regulatory environments. Successful organizations develop localized strategies while maintaining core brand identity.
Streamlined Operations
Integrated digital systems optimize supply chains and inventory management through real-time data synchronization. Automated processes reduce operational friction while improving accuracy and speed.
Intelligent automation significantly enhances productivity by handling repetitive tasks, allowing human resources to focus on strategic initiatives. These efficiency gains translate directly to improved profitability and service quality.
Security Considerations
While digital transformation offers substantial benefits, it introduces complex security challenges. Protecting sensitive information and system integrity requires continuous vigilance and investment.
Comprehensive security frameworks and employee awareness training form essential defenses against evolving cyber threats. Regular system updates and strict access controls help mitigate potential vulnerabilities in interconnected environments.
Beyond the Vehicle: Securing the Entire Ecosystem
Protecting the Connected Car Ecosystem: A Holistic Approach
The modern vehicle represents a sophisticated technological network encompassing numerous integrated systems. This complexity demands comprehensive security strategies that address potential vulnerabilities across all components.
Effective protection requires defense-in-depth methodologies that anticipate threats at every system layer. Such comprehensive safeguards help prevent unauthorized access to sensitive data and critical vehicle functions.
The Role of Cloud Security in Connected Car Safety
Cloud infrastructure supports essential vehicle functions through data processing and remote functionality. Securing these distributed systems prevents potential compromise of user privacy or vehicle operation.
Securing Communication Channels: A Critical Component
Vehicle connectivity relies on multiple communication protocols that require robust encryption and authentication. Continuous monitoring helps detect and prevent potential interception or manipulation attempts.
Data Protection and Privacy in the Connected Car
Modern vehicles generate extensive operational and personal data requiring stringent protection measures. Implementation of advanced encryption and access management systems helps maintain user trust and regulatory compliance.
Software Updates and Vulnerabilities: A Constant Battle
Continuous software evolution necessitates rigorous security testing throughout development cycles. Automated vulnerability detection and rapid patch deployment help maintain system integrity against emerging threats.
The Importance of Human Factors in Connected Car Security
User education complements technical safeguards by promoting secure interaction with vehicle systems. Simplified security interfaces encourage proper use of protective features by all operators.